The pen tester starts off on the same footing that a real hacker would. It simulates the actions and procedures of a real attacker by severely limiting the information given to the person or team performing the test beforehand.
What Are The Different Types Of Penetration Testing Purplesec
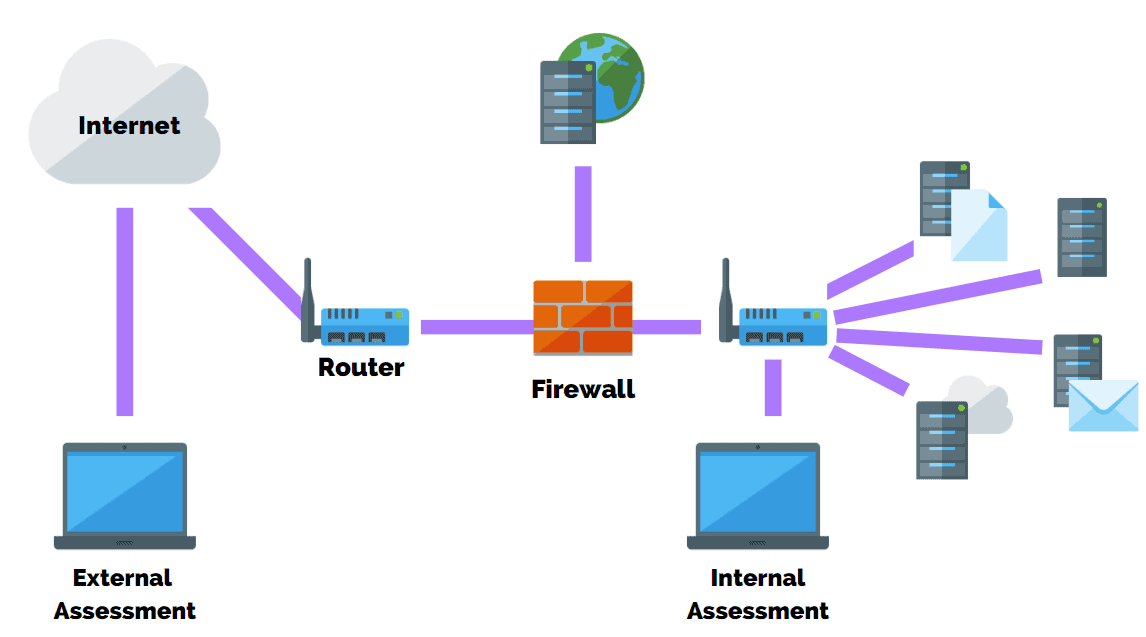
Pen testing focuses on all areas of a companys infrastructure whether on-premise or in the cloud.
. The following points give general activities aimed at. Pen testing can involve the attempted breaching of any number of. Pentesting is a process where testers attempt to access or exploit vulnerabilities in your organizations computer systems networks websites and applications.
Additionally the pen tester may attempt to crack the password hashes she collected during reconnaissance. Internal penetration testing simulates an attack on your organization that originates from within it. InfrastructureNetwork Pen Test.
All our penetration tests include a vulnerability assessment as part of. What is an external pentest. Gray box testing d.
Pen testing acts as a simulated cyberattack aiming to evaluate the effectiveness of your organizations security measures and let you know if you need to make any improvements. In the context of web application security penetration testing is commonly used to augment a web application firewall WAF. PCI pen test to assess the technical and operational components of your system to ensure cardholder and payment data security systems meet the set PCI compliance standards.
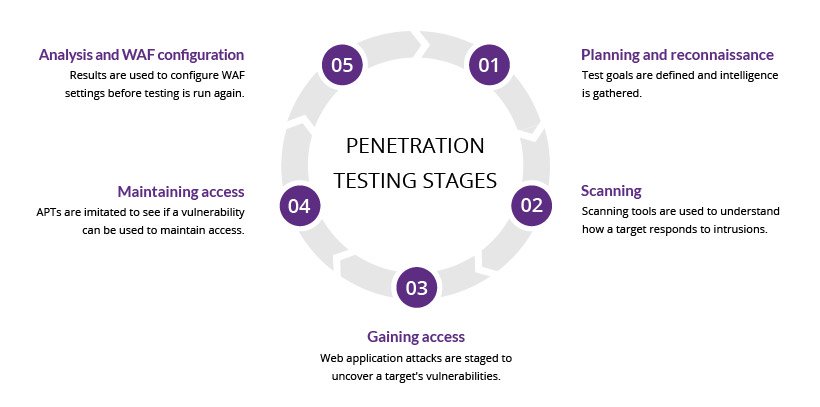
Penetration testing also sometimes referred to as ethical hacking is the terminology used by members of the information technology security community to describe an authorized assessment that simulates the. The aim of conducting a pen test is to understand what vulnerabilities are in your business systems how. Which of the following is a test wherein the pen-tester has partial knowledge about the target systemnetwork.
The tests aim to determine how easily identifiable a target an organizations ICT. Which of the following BEST describes an unknown penetration test. Several pieces of.
This approach conducted by a skilled professional helps you identify possible attack routes and vulnerabilities that may not be found from vulnerability assessments. Independence Tara recently analyzed the results of a vulnerability scan report and found that a vulnerability reported by the scanner did not exist because the system was actually patched as specified. For example the pen testers may only be.
A penetration test also known as a pen test is a simulated cyber attack against your computer system to check for exploitable vulnerabilities. Pen testing can include the following things. Internal Testing helps estimate how much damage a disgruntled employee could cause.
Although expensive blind pen testing is highly efficient. External penetration testing simulates the most common approach used to hack a companys systems performed remotely from the internet. Pentesting tests helps an organization to do the following except.
With the double-blind penetration testing method employees are unaware that a pentest has been performed. A penetration test commonly known as a pentest is a security assessment which simulates the malicious activities of real-world attackers to identify security holes in your businesss systems or applications. In the end an internal pen test can provide organizations with an instant picture of the biggest risks to their network infrastructure based on the overall security of their internal IT.
The names or types of these test vary but what is important is that the following areas are tested. It takes a lot of time and effort to complete with various penetration testing tools to plan and execute the entire exercise. The following article presents the differences between internal external testing and where they fit into a companys risk management strategy.
This means they begin with little to no information about the IT infrastructure and security defenses. External penetration testing is a practice that assesses the externally facing assets for an organization. Many organizations make assumptions regarding the security and integrity of their IT systems and network without ever confirming that these assumptions are valid.
False Internal testing simulates what. Penetration testing can be carried out using a wide range of tools or with a vendor provided solution 16. The hired hacker simulates.
Which type of testing is typically done by an internal tester who has full knowledge of the network computer system and infrastructure. Internal network penetration testing simulates the actions of a skilled attacker and helps you find network security gaps that create security exposure and risk. White box testing c.
Which of the following is one of the important documents to be signed before the penetration test to safeguard interest of the concerned parties. A penetration test simulates the tools and techniques of an attacker to detect and exploit vulnerabilities. Following the completion of the internal pen test the pentester and security team must report to the senior staff and possibly the board andor sta.
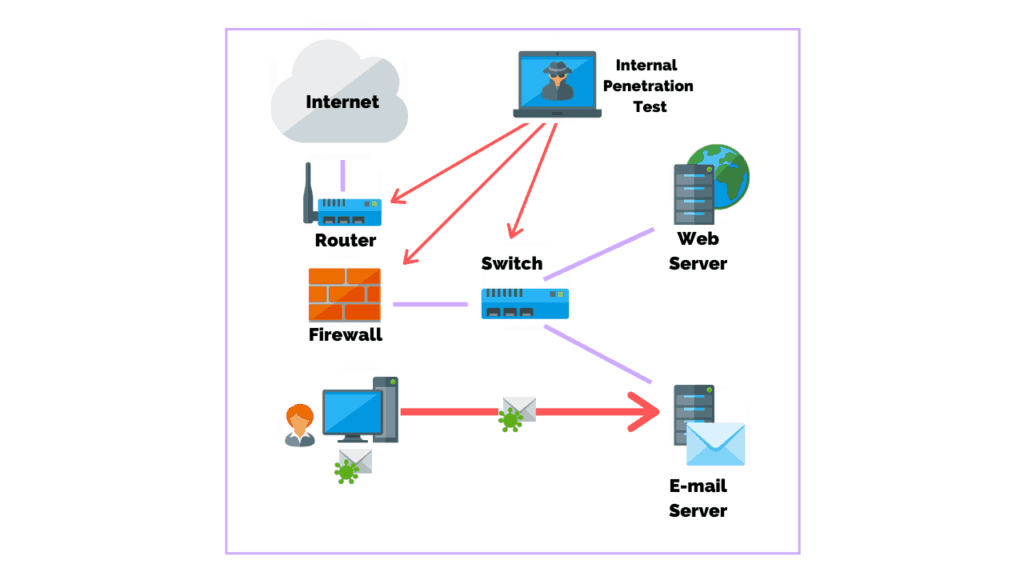
Unlike external penetration testing internal testing assumes the attacker already. Ways to Perform Pen Tests. Which type of test simulates an insider threat by giving the tester partial information about the network and computer systems.
An internal penetration test simulates an attacker attacking the components of an information system from within the company. The targets are the same as external pentesting but the difference is the attacker either has authorized access or is starting from a point within the internal network. Alternatively the tester may attempt to gain access to privileged data.
Simulates the damage that employees could wreak on your systems. 21 External testing simulates what an insider attack could accomplish. It uses a distinctly different approach from external penetration testing which testers usually perform first.
Which of the following is NOT a benefit of using an internal penetration test team. During our internal network penetration testing service NetSPI identifies security vulnerabilities such as patch configuration and code issues at the network system and. Black box testing b.
Commonly referred to as an Internal Pen Test the internal infrastructure penetration test focuses on testing attacks which could be carried out by an adversary who has already gained a foothold within your network and is looking to elevate themselves to gain further control and cause more damage. The following are four ways of performing a pen test. During an external penetration test the assessor attempts to gain entry into the internal network by leveraging vulnerabilities discovered on the external assets.
The main goal in external pentesting is to identify and. During the internal penetration testing attack the tester looks specifically for the following issues. Internal testing focuses on the devices such as firewalls servers routers or switches that could come under attack.
Internal network penetration testing focuses on identifying the risks posed by an attacker with internal access to a network to compromise that system. Black-box testing also known as external penetration testing simulates an attack from outside of your organization. Internal testing simulates what an insider attack could accomplish.
Penetration testing simulates a real-time attack and determines the impact on the business if an attack was successful.

What Is Penetration Testing Definition Stages Techniques Pros And Cons

Professional Pen Testing Company Penetration Testing Service
External Vs Internal Penetration Test What S The Difference
What Are The Different Types Of Penetration Testing Purplesec
0 Comments